How does Multi-Party Computation help to build a Keyless wallet?
Transforming crypto security: Keyless wallets with MPC and Self Chain for risk-free asset management.

Introducing Threshold Signature Scheme (TSS), a type of digital signature protocol used by Multi-parity Computation.
The concept of TSS is similar to how Multisig wallets work with a significant difference. In the case of multi-sig setup, there are m distinct wallets, to perform cryptographic operations i.e. signing a transaction n of those wallets are required to co-sign the same message. The verification process differs based on the blockchains.
In the Threshold Signature Scheme, we will have “m of n” setups, none of these entities processes, and a valid private key. Each entity will hold a private share (some piece of data) and when it comes to signing a transaction, they will collectively work together, each using their private share and create one holistic valid digital signature. n private shares will combine to create one single private key (as a consequence, one single wallet address).
In TSS, there is no party that can hold or process the private key and there is no concept of private key re-creation. The signing process is part of the MPC protocol where parties collectively provide private input to a specific function (digital signing process) and compute the output of that function (digital signature).
Therefore, the privacy and security features are preserved. No point in any parties can individually signing a message using their private share. This is why TSS will be a good candidate technology to build a keyless crypto wallet.
The old Approach and it’s problem
The current non-custodian wallets are cumbersome. Alice a nontechnical person downloads a crypto wallet app. During the onboarding process, she is asked to back up a weird list of words by writing them down on paper. Although she doesn’t really understand why she has to do it, she does follow the instructions and backs up those words.
Things go well until her phone is broken. With a new phone, she downloads the wallet app again. Surprisingly, she is asked to provide those 12 or 24 words to recover her wallet. Unfortunately, she lost the paper and she didn't have the word backups on Cloud. After reaching the support team she came to the conclusion that her crypto assets are gone.
Let’s imagine, that Alice did upload the file on her Cloud account. She would be able to restore her wallet. There is another very important challenge here though, what if her Cloud gets hacked? The answer is obvious, the hacked will have access to those weird words.
MPC comes in to build a better wallet for non-technical users
A Keyless wallet built with MPC will not ask users to back up the recovery words. The onboarding process would look like below:
- Alice downloads the wallet.
- She enters her phone number or email (no username or password) or can even use her social media accounts.
- That's it from Alice's perspective.
Behind the sense, MPC will help to simplify the complicated process:
- After Alice has successfully logged in, the wallet app will use the embedded MPC component to initiate the key generation process.
- The wallet app API will also create a private share for Alice and will join the key generation process.
- MPC requires all parties to work together. Thus there needs to be a way to communicate with each other and keep the state of each step processed. This is what the State Machine does. We could alternatively use a p2p network or even an entire blockchain to act as the state machine. this is precisely what Self Chain was built for.
- Once the MPC protocol has finished, each party will have a private share.
After the wallet creation, 1 of the "s" shares will be sent to Alice through her email or phone number. She can use this share to recover her wallet later.
Backup private shares
The backup will have to happen on the two private shares, both the mobile app, as well as, the MPC API would have to make sure that the private shares are stored somewhere they both can restore them when needed.
Client-side backup
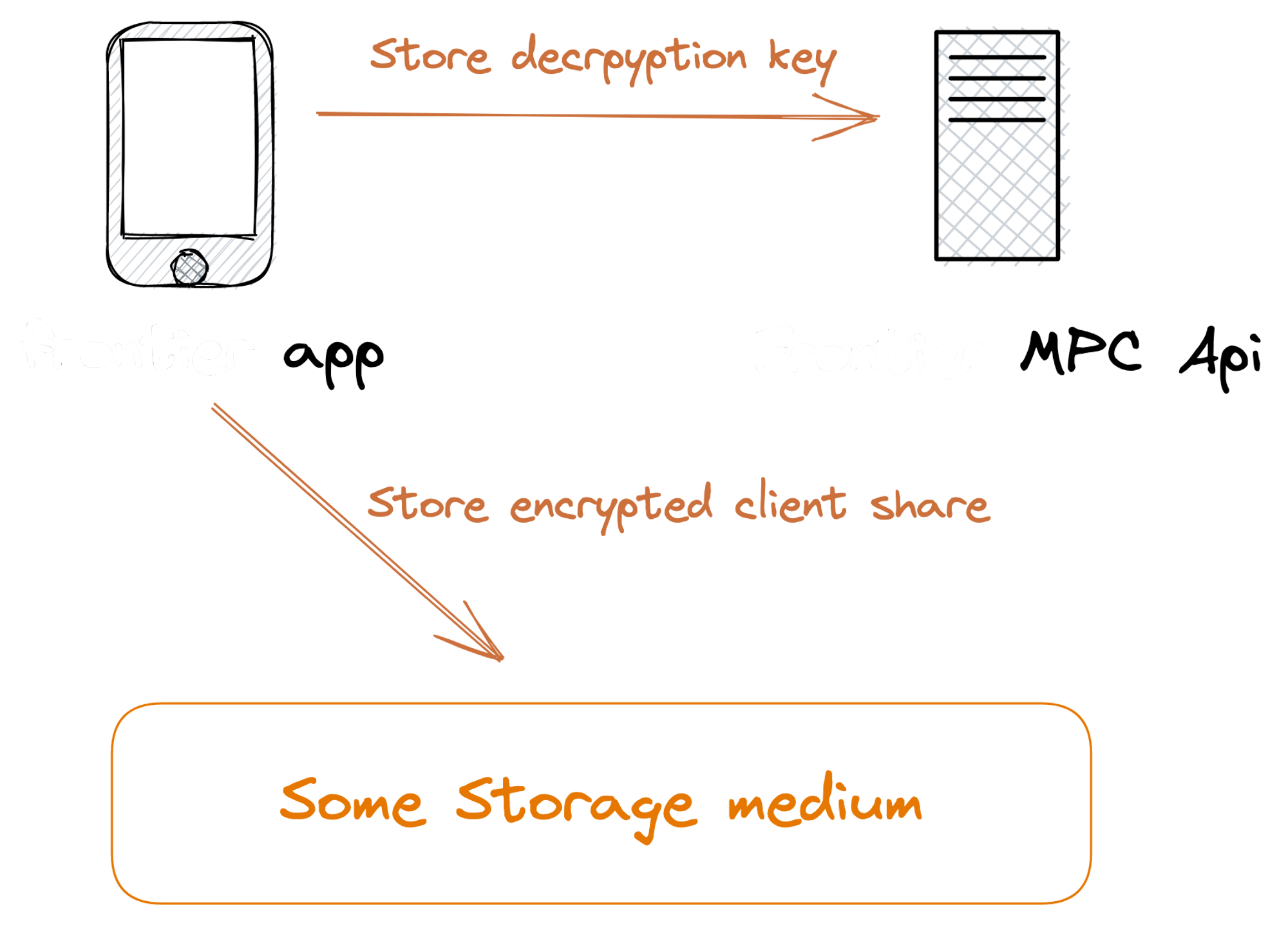
- The wallet app will create a unique symmetric key.
- It will use the key to encrypt the client's private share.
- It will post this encrypted client share to Self Chain as a storage medium.
- It will finally post the decryption key to the Wallet MPC API.
Restoring the key would follow the opposite direction:
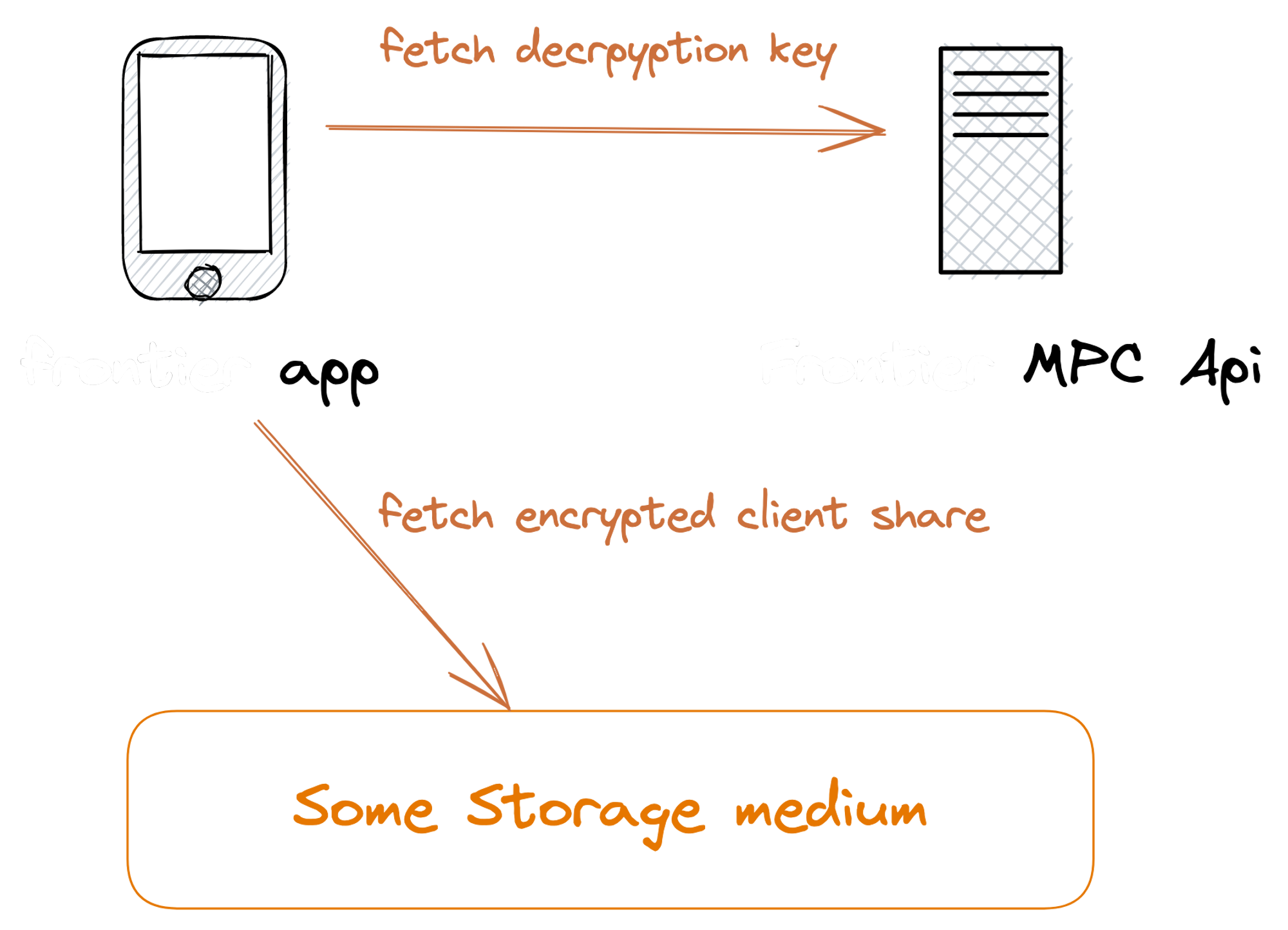
- After the user has logged in, the wallet app will fetch the encrypted share from Self Chain.
- It will request the decryption key from Wallet MPC API.
- It will use the decryption key to decrypt the client share.
- The client-side share is restored. as well as the wallet.
Alice doesn't need to worry about the recovery words, all she needs is to store a small piece of share that will need for the recovery process later. The Wallet MPC API and the Self Chain will do the rest of the job to keep her crypto assets safe.
The Case for Self Chain
At this point, we can simply reveal what this cryptic “some storage medium” is. It will be the Self Chain. The purpose of the chain is to store the encrypted client-side backups, as well as, the master decryption key from the previous section.
In the future, we could think of a way to make the Self Chain one of the parties in the MPC protocol.
We could also use the Self Chain as the state machine depicted in the high-level architecture described above.
About Self Chain
Welcome to Self Chain, a Layer 1 blockchain designed for trustless, next-generation key management. Self Chain offers a secure infrastructure for keyless wallets and ensures enhanced security and user control through advanced technologies like Multi-Party Computation (MPC) and Threshold Signature Scheme (TSS).
Join us as we shape the future of finance, privacy, and digital ownership. Unlock the true potential of blockchain technology with Self Chain and be part of the decentralized movement.
